A new variant of the SamSam ransomware has recently been detected. It is equally robust as its popular version which caused widespread damage with its high profile attack to state agencies, hospitals, city councils, and more.
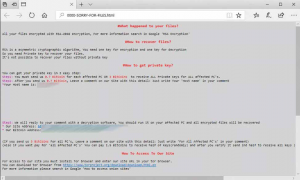
This newly discovered, more targeted Samsam variant utilizes new techniques and alterations making it unique and more difficult to spot – it requires user interaction to start its attack. It will not execute unless the attacker running the payload manually enters a special password (via the command line) before infecting any system. This means that only the person/s who know the author’s passcode can run the ransomware. Moreover, even if the ransomware is already inside one’s system, it will not infect unless the password has already been entered. This gives researchers a hard time executing the ransomware binary or run on their test machine unless they knew the password.
SamSam ransomware has remained a nasty yet elusive malware. It gained its worldwide notoriety when it infected Atlanta City’s IT systems, the Colorado Department of Transportation, and several health care organisations compromising data security and leaving millions of dollars in losses.
To get protected against this notorious ransomware, basic security practices like secured passwords, performing regular backups, and employing a centralized patch management system is crucial. These will not only keep potential hackers out of your system but you will also be able to limit any damage caused and easily recover from a ransomware attack.