Have you recently received an email saying your device was compromised? Below is its full content.
I am sorry to inform you that your device was compromised.
I’ll explain what led to all of this. I have used a Zero Day vulnerability with a special code to infect your device through a website.
This is a complicated software that requires precise skills that I have. It works as a chain with specially crafted and unique code and that’s why this type of an attack can go undetected.
You only need one not patched vulnerability to be infected, and unfortunately for you – it works that simple.
You were not targeted specifically, but just became one of the quite a few unlucky people who got hacked that day.
All of this happened a few month ago. So I’ve had time to collect information on you.
I think you already know what is going to happen next.
During that time, my software was quietly collecting c
There is more to it, but I have listed a few reasons for you to understand how serious this is.
For you to clearly understand, my software controlled your camera and microphone as well and it was impossible for you to know about it.
It was just about right timing for me to get you privacy violated.
I’ve been waiting enough and have decided that it’s time to put an end to this.
So here is my offer. Let’s name this a “consulting fee” I need to delete the media content I have been collecting.
Your privacy stays untouched, if I get the payment.
Otherwise, I will leak the most damaging content to your contacts and post it to a public tube for perverts to explore.
I understand how damaging this will be for you, and amount is not that big for you to keep your privacy.
Please dont blame me – we all have different ways of making a living.
I have no intention of destroying your reputation or life, but only if I get paid.
I don’t care about you personally, that’s why you can be sure that all files I have and software on your device will be deleted immediately after I receive the transfer.
I only care about getting paid.
My modest consulting fee is 1650 US Dollars transferred in Bitcoin. Exchange rate at the time of the transfer.
You need to send that amount to this wallet:
The fee is non negotiable, to be transferred within 2 business days.
We use Bitcoin to protect my identity.
Obviously do not try to ask for any help from anybody unless you want your privacy to violated.
I will monitor your every move until I get paid. If you keep your end of the agreement, you wont hear from me ever again.
Take care.
Don’t fall for the trap and don’t pay any ransom fees! These scammers don’t have any compromising or embarrassing photos of you. This said email is a scam which will try to extort the receiver into paying $1650 in BitCoin. Avoid clicking any link. Simply ignore and delete these kind of emails.
With software, you can remove the ‘Your device was compromised’ email scam easily. You may have received this email and was downloaded on your computer for many reasons such as clicking malicious websites, codecs, or downloads. Be sure to remove it immediately.
To remove the "Your device was compromised" Email Scam, simply follow this guide:
STEP 1: Uninstall "Your device was compromised" Email Scam from Windows
The first thing that needs to be done - "Your device was compromised" Email Scam should be uninstalled through the Windows Control Panel.
1 Access the uninstall menu.
1 For Windows 8 or Windows 10, to uninstall a specific program, you must right-click the Windows Start button and select Control Panel from ensuing the pop-up menu.
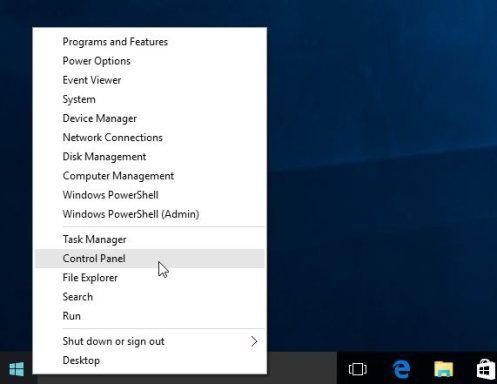
2 Once the Control Panel is open, go to the Programs category, and click on Uninstall a program underneath it.
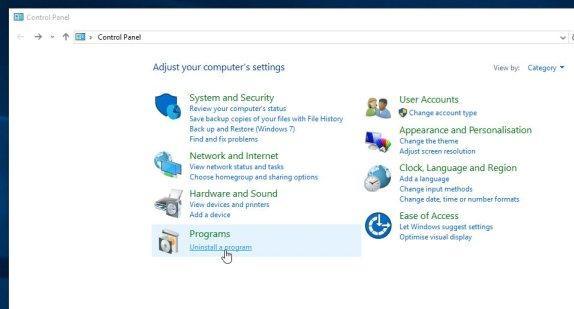
1 For Windows XP, Vista, and 7, simply click the “Start button” and press “Control Panel”.
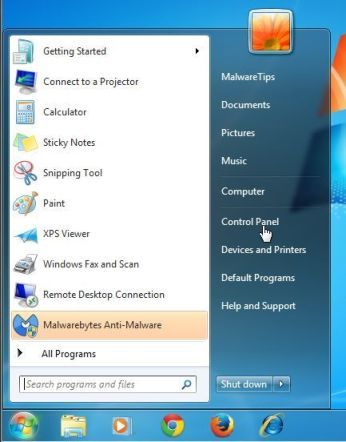
2 When the “Control Panel” window opens click on the “Uninstall a program” option under “Programs” category.
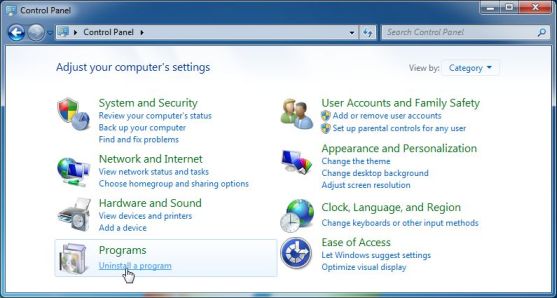
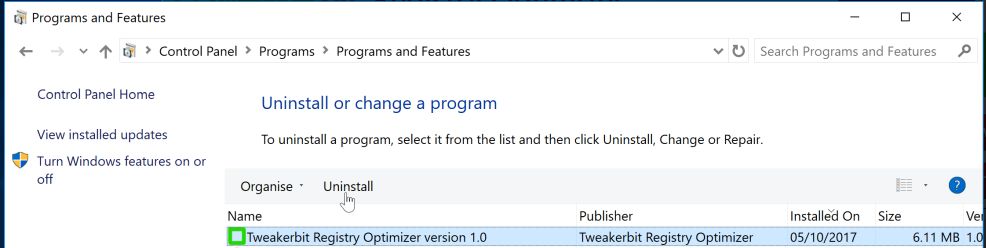
2 Programs and Features will then be displayed. Look through the installed programs, find "Your device was compromised" Email Scam and uninstall it.
Tip: To sort by most recently installed programs, click the “Installed On”. You will likely find it near the top.
Now go over the list and start uninstalling any unwanted or unknown programs. If you cannot find any of these on your system, then you can proceed with the next step.
STEP 2: Run Malwarebytes to Scan for Spyware, Viruses, and Adware.
Malwarebytes is an advanced utility which will scan and automatically remove from your computer or laptop any malicious program that may have been installed along with "Your device was compromised" Email Scam. Do note that Malwarebytes will run alongside any antivirus software without conflicts.
1 You can start downloading Malwarebytes from this link: Download Malwarebytes
2 Once the download is finished, double click the installation file to begin. Allow Malwarebytes to make changes to your device, and continue clicking “Next” until the software is installed and click “Finish”.
3 Malwarebytes should automatically launch from here but if not just double click the new program. To start a system scan, click on the Scan Now button.
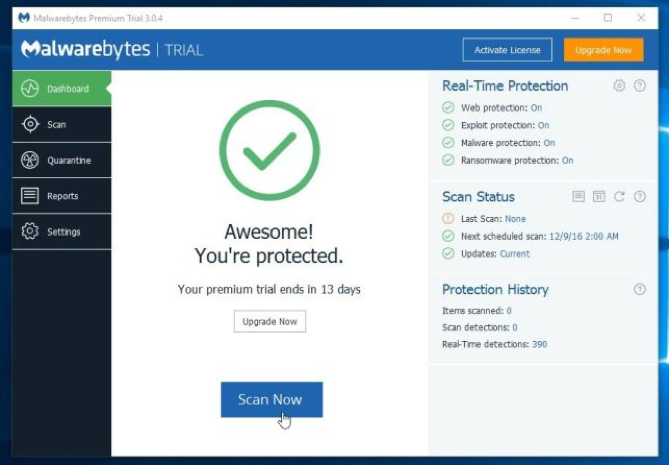
The scan will begin and start checking your computer for "Your device was compromised" Email Scam and any other potential malware. The scan process could take anywhere from a few minutes to thirty minutes, depending on the size of your hard disk and the amount of infections found.
4 Once the scan is completed, select all of the detected threats and click the Quarantined Selected” button.
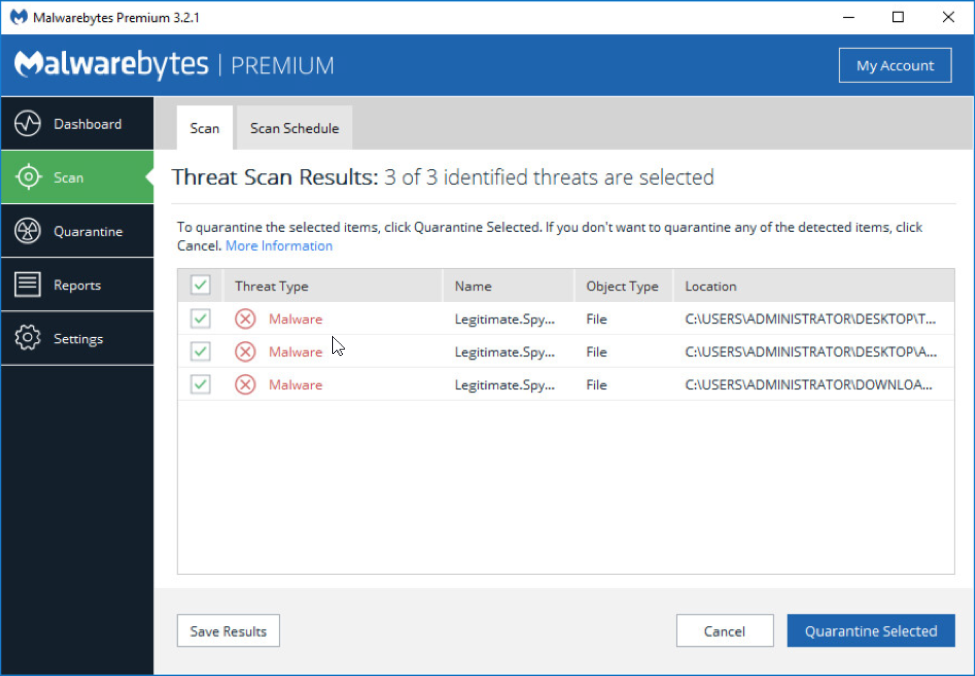
Once the quarantine is finished, you can select to “Delete All” of the infections. You may have to restart your computer to finish the removal process.
Congratulations, your computer is now free of "Your device was compromised" Email Scam. Your computer should also boot up and perform much faster than before.
STEP 3: Run AdwCleaner to check for any lingering adware on your computer.
AdwCleaner is a wonderful tool to help remove any Adware that might have been installed on your computer as a result of "Your device was compromised" Email Scam.
Unfortunately, infections spread once installed on your machine and attempt to hijack your browser, add unwanted programs, and install toolbars without your permission.
1 To begin click here to download AdwCleaner – Download Link
Double click the file and run the installer. Make sure you allow AdwCleaner to make changes to your device.
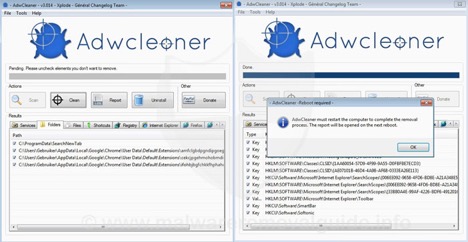
2 Once install run a scan by clicking the “Scan” button. This process could take anywhere from a few minutes to thirty minutes.

3 When the scan is complete click the “Clean” button to remove any infections that were found. The software will also ask that you reboot your computer to complete the removal process.
Tips for Keeping your Computer Protected from viruses like "Your device was compromised" Email Scam
1 Use a powerful professional antivirus software that provides frequent updates to protect against the latest threats. New viruses are being released every day, it’s important to have a software that is on top of all the new infections.
2Install a real-time antivirus software and firewall to protect against threats as they occur.
3Don’t download software from unverified websites. Often times these programs come bundled with Adware and other harmful applications.
4Don’t open email attachments from people you don’t know. Moreover, don’t open links to suspicious emails from people you DO know. Often times spammers will send viruses by hacking into a friends’ email and blasting out dangerous links. If it looks suspicious, ask the person if they had intended to send it or not.
5Don’t fall for virus hoaxes. If you get sudden warnings about your computer being infected, particularly after being redirected on a website, don’t fall for the trap. They are trying to scare you into downloading a virus. Click out of it and then run an antivirus software right away to ensure your system was not breached.